Enable Single Sign-On / SAML 2.0
Enable your team to log in using your organization’s identity provider credentials
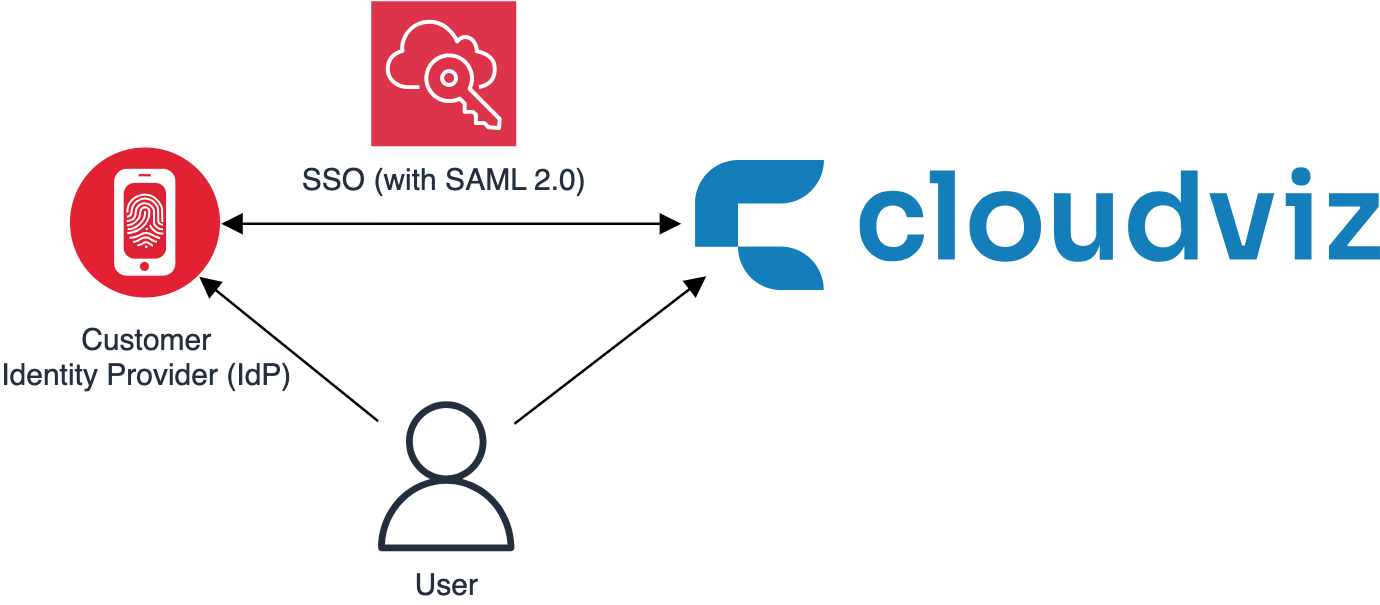
Overview
Cloudviz.io supports SSO authentication via the Security Assertion Markup Language 2.0 (SAML 2.0). Enabling SAML SSO for your account allows you and your team to log in using credentials stored in your organization’s Active Directory, LDAP, or any other identity store connected to a SAML Identity Provider.
Enabling SAML SSO
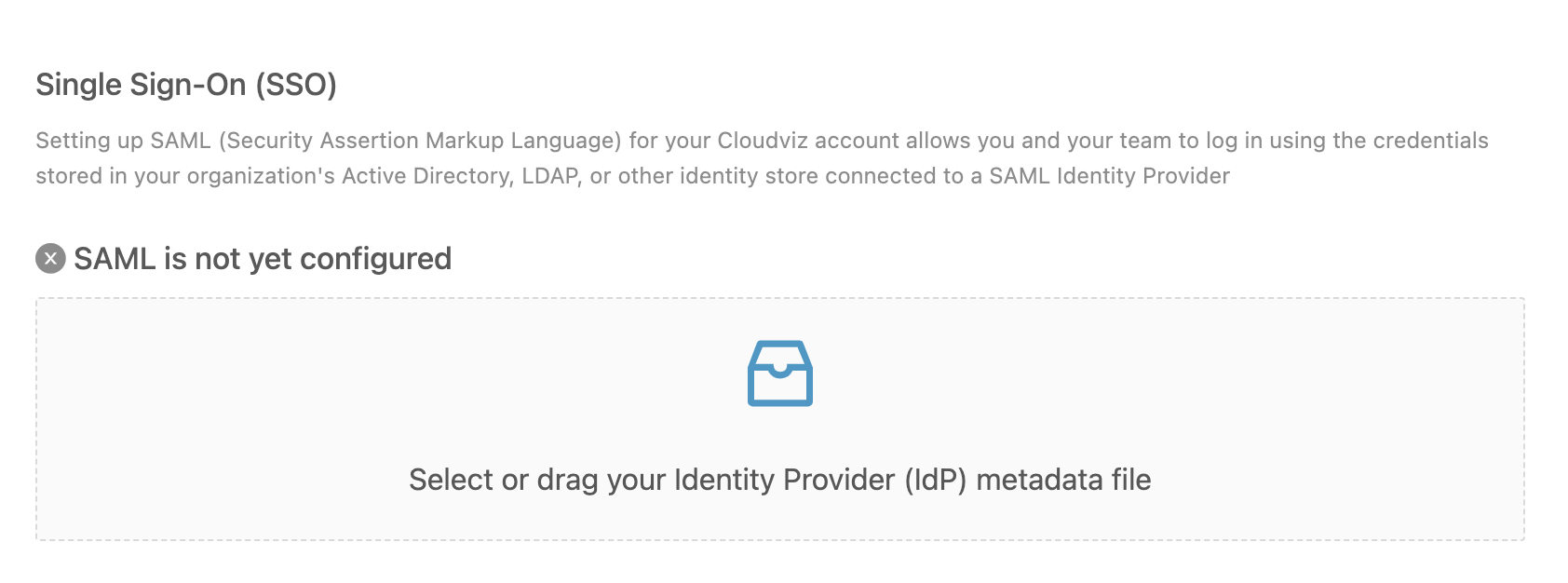
To enable SAML SSO for your account, you must be an owner with an active Team subscription. Follow these steps to set up SAML SSO:
- Navigate to Settings > Security & SSO.
- Create Cloudviz.io as a new application in your Identity Provider (see Enable SSO with Okta, Enable SSO with Azure AD
) using the service provider details provided in the Security & SSO section:
- Assertion Consumer Service URL
- Service Provider Entity ID
- NameId Format
- Map the email attribute in your IdP SAML configuration so that it appears in the SAML response as
<saml:Attribute Name="email" ...>. - After creating the application, return to Cloudviz.io and upload the metadata file from your Identity Provider.
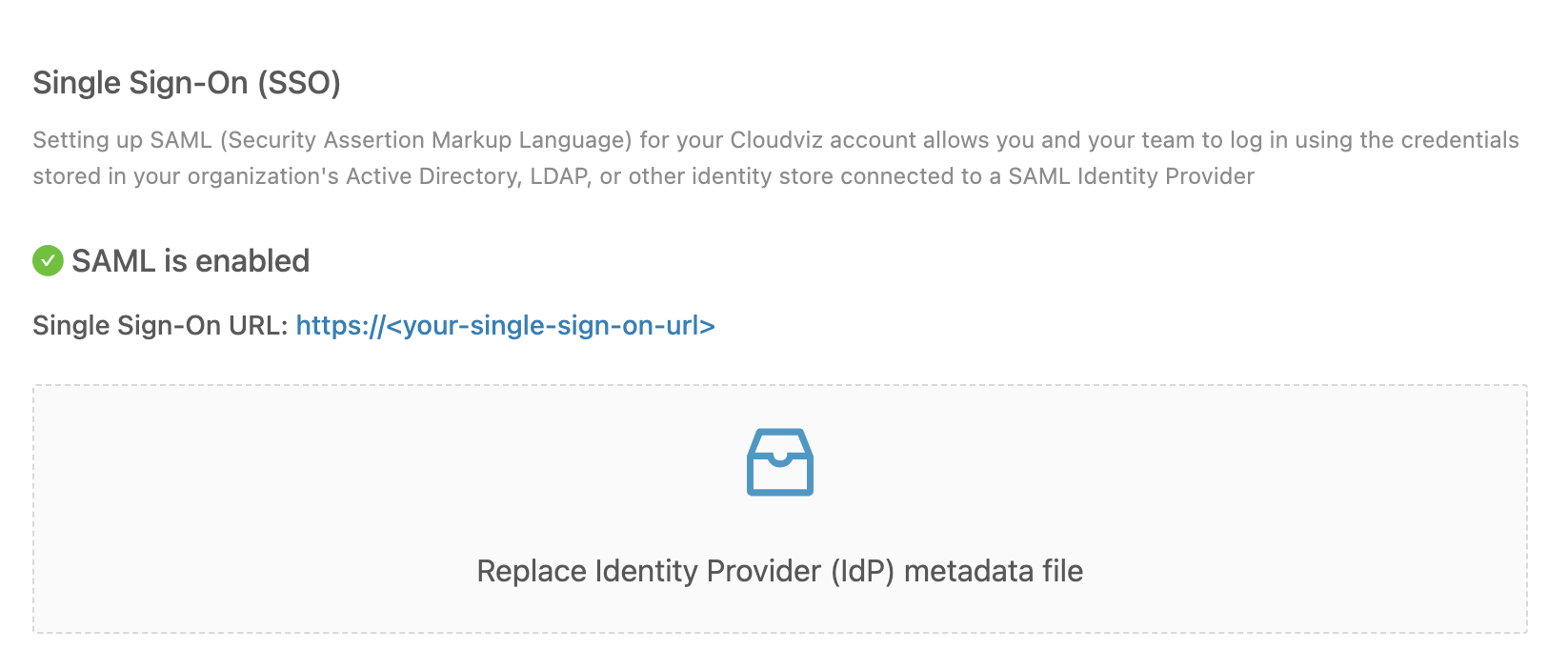
- Once the configuration is successful, you will see an indication that “SAML is enabled” along with the “Single Sign-On URL.” Allow a few seconds for the URL to become fully operational.
Advanced SAML SSO Features
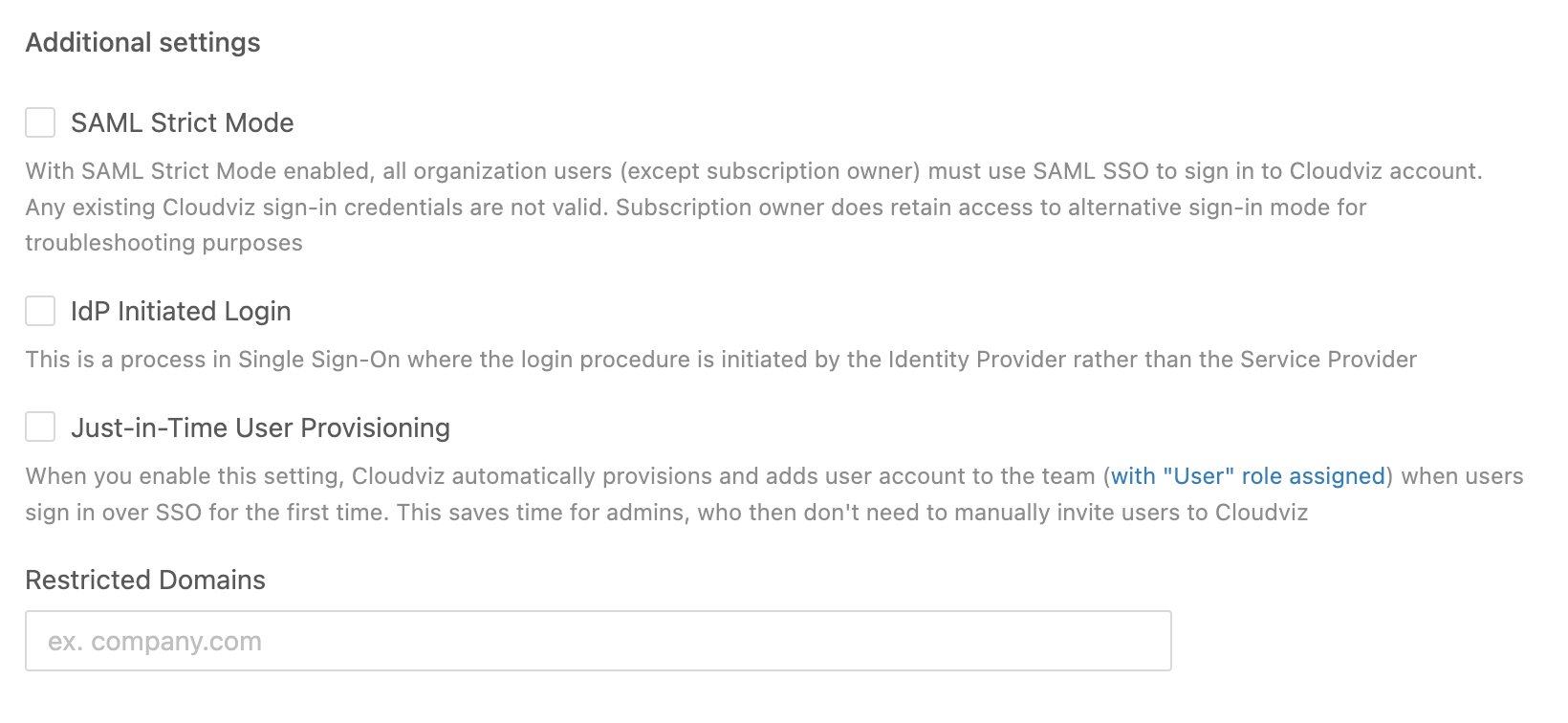
We support several advanced features to enhance your SAML SSO experience:
- SAML Strict Mode: With this mode enabled, all organization users (except the subscription owner) must use SAML SSO to sign in. Existing Cloudviz.io credentials will no longer be valid, although the subscription owner retains an alternative sign-in mode for troubleshooting.
- IdP Initiated Login: The login process can be initiated by the Identity Provider rather than by Cloudviz.io.
- Just-in-Time User Provisioning: When enabled, app automatically provisions a new user account (with the User role) the first time someone logs in via SSO. This eliminates the need for manual user invitations.
- Restricted Domains: Limit SSO authentication so that only users with email addresses from specified domains are allowed access.
Disabling SAML SSO
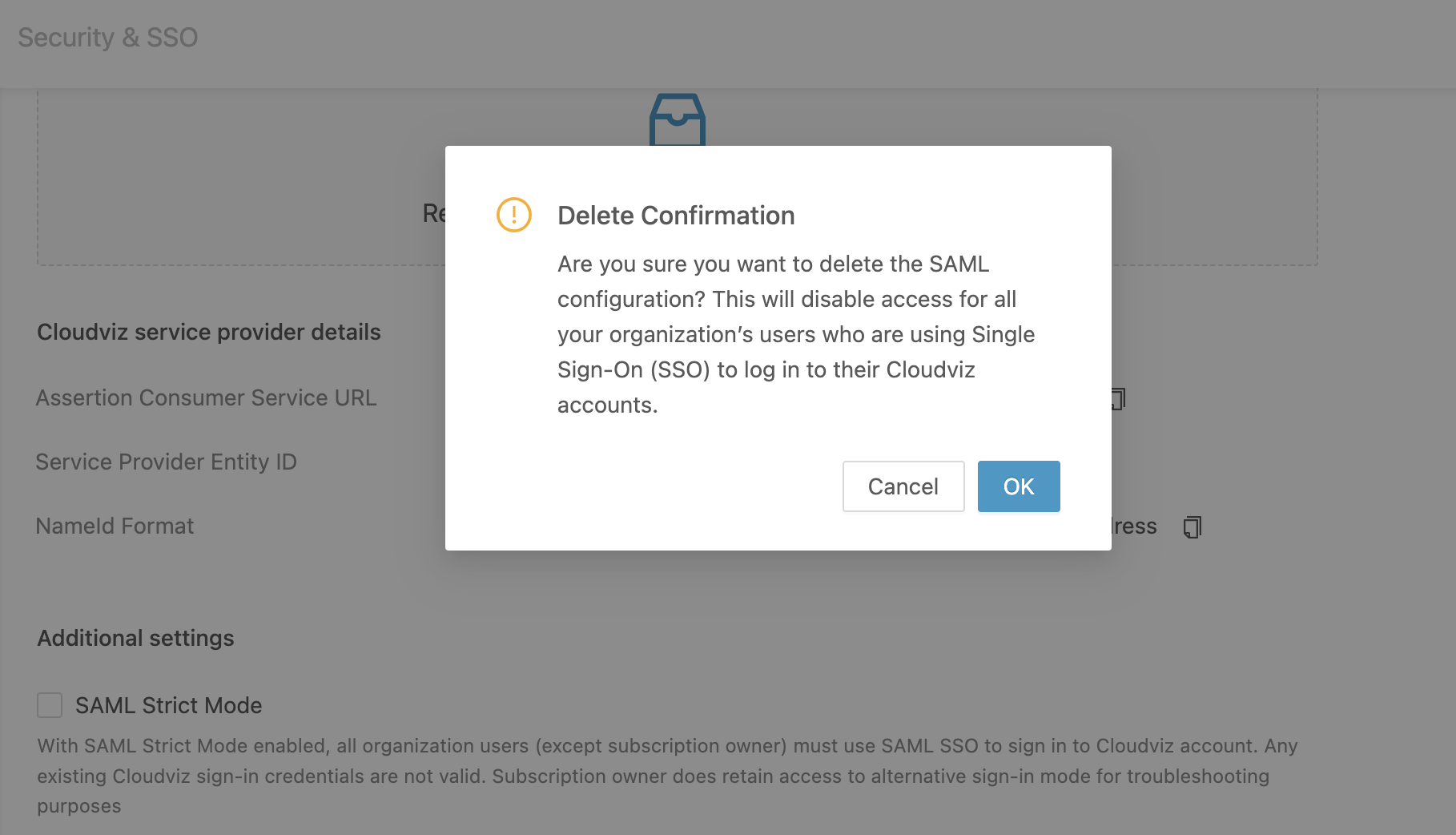
To disable SAML SSO, go to Settings > Security & SSO and click the Delete configuration button. This action removes your SAML configuration and disables SSO access for users who rely solely on this method for authentication.
Managing SAML User Deletion
Due to SAML limitations, our app does not receive notifications when a user’s access is revoked in the IdP. Once a user’s session expires, any subsequent SSO login attempts will be denied. For immediate effect, remove the user directly from the Cloudviz.io team through the app. It is recommended to review your team membership regularly and remove users who no longer require access.